Firebase-tools: ADC Auth error: Scopes are required for this request
Hi, I’m trying to automate the deployment of firebase functions. When I run something like “GOOGLE_APPLICATION_CREDENTIALS=
Version info
3.18.5
Platform Information
container node:6.14-alpine
Steps to reproduce
/usr/bin/docker run --rm -v /workspace:/workspace -e GOOGLE_APPLICATION_CREDENTIALS=
Expected behavior
To be authenticated
Actual behavior
[2018-05-29T15:57:32.507Z] > command requires scopes: [“email”,“openid”,“https://www.googleapis.com/auth/cloudplatformprojects.readonly“,”https://www.googleapis.com/auth/firebase”]
[2018-05-29T15:57:32.507Z] > attempting to authenticate via app default credentials
[2018-05-29T15:57:32.547Z] ! auto-auth error: Scopes are required for this request.
[2018-05-29T15:57:32.547Z] > no credentials could be found or automatically retrieved
Do you have some suggestions?
All 46 comments
Hi, the credentials required is not GOOGLE_APPLICATION_CREDENTIALS, so that line doesn't actually help you.
You'll need to generate a CI token and then run the command with the --token flag, see https://github.com/firebase/firebase-tools#using-with-ci-systems for more info.
Hi,
and what about https://github.com/firebase/firebase-tools/pull/417 ?
It seems that GOOGLE_APPLICATION_CREDENTIALS is implemented and firebase-tools uses google-auto-auth to obtain that.
Or I'm wrong?
I would not use CI token because I wouldlike to authenticate with a service account and not a Google user (GSuite or Cloud Identity or whatever else)
Thank you
Hi,
it seems the library make a call to firebase-public.firebaseio.com:443 and has a HTTP return code of 200 but a response of 0 bytes
Hi, you're right. Sorry, I forgot about that PR. I'm not super familiar with this. Michael, can you take a look when you are back in the office?
Hi @laurenzlong @mbleigh ,
I've found that configuring "Domain Wide Authority" for the service account permit to authenticate.
But now I've the following problem:
GOOGLE_APPLICATION_CREDENTIALS=<path_to_json> firebase deploy --only functions --non-interactive --project=<project_id> --debug
[2018-06-04T09:25:46.202Z] ----------------------------------------------------------------------
[2018-06-04T09:25:46.211Z] CLI Version: 3.18.5
[2018-06-04T09:25:46.212Z] Platform: linux
[2018-06-04T09:25:46.212Z] Node Version: v6.14.2
[2018-06-04T09:25:46.212Z] Time: Mon Jun 04 2018 09:25:46 GMT+0000 (UTC)
[2018-06-04T09:25:46.213Z] ----------------------------------------------------------------------
[2018-06-04T09:25:46.238Z] > command requires scopes: ["email","openid","https://www.googleapis.com/auth/cloudplatformprojects.readonly","https://www.googleapis.com/auth/firebase","https://www.googleapis.com/auth/cloud-platform"]
[2018-06-04T09:25:46.238Z] > attempting to authenticate via app default credentials
[2018-06-04T09:25:46.445Z] xxxx.x.xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx-xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx-xx
[2018-06-04T09:25:46.446Z] > retrieved access token via default credentials
[2018-06-04T09:25:46.449Z] >>> HTTP REQUEST GET https://admin.firebase.com/v1/projects/<project_id>
Mon Jun 04 2018 09:25:46 GMT+0000 (UTC)
[2018-06-04T09:25:47.067Z] <<< HTTP RESPONSE 404 server=nginx, date=Mon, 04 Jun 2018 09:25:47 GMT, content-type=application/json; charset=utf-8, content-length=87, connection=close, x-content-type-options=nosniff
[2018-06-04T09:25:47.069Z] <<< HTTP RESPONSE BODY code=PROJECT_NOT_FOUND, message=The specified project was not found.
The service account has Editor permissions on the project, and if I use a Google identity (not a svc account) the problem doesn't exists
I've found this similar issue (but they use token) https://github.com/firebase/firebase-tools/issues/744
Thanks
No, I'm wrong.
If i execute firebase use I have again:
[2018-06-04T14:39:38.660Z] > command requires scopes: ["email","openid","https://www.googleapis.com/auth/cloudplatformprojects.readonly","https://www.googleapis.com/auth/firebase"]
[2018-06-04T14:39:38.660Z] > attempting to authenticate via app default credentials
[2018-06-04T14:39:38.693Z] ! auto-auth error: Scopes are required for this request.
[2018-06-04T14:39:38.694Z] > no credentials could be found or automatically retrieved
Same behaviour even with a service-account having the Owner role assigned trying to do anything using the firebase CLI tool:
$ export GOOGLE_APPLICATION_CREDENTIALS=account.json
$ firebase list --debug
[2018-06-05T12:15:17.340Z] ----------------------------------------------------------------------
[2018-06-05T12:15:17.343Z] Command: /usr/local/bin/node /usr/local/bin/firebase list --debug
[2018-06-05T12:15:17.343Z] CLI Version: 3.18.5
[2018-06-05T12:15:17.343Z] Platform: linux
[2018-06-05T12:15:17.343Z] Node Version: v10.3.0
[2018-06-05T12:15:17.343Z] Time: Tue Jun 05 2018 12:15:17 GMT+0000 (UTC)
[2018-06-05T12:15:17.343Z] ----------------------------------------------------------------------
[2018-06-05T12:15:17.347Z] > command requires scopes: ["email","openid","https://www.googleapis.com/auth/cloudplatformprojects.readonly","https://www.googleapis.com/auth/firebase"]
[2018-06-05T12:15:17.348Z] > attempting to authenticate via app default credentials
[2018-06-05T12:15:17.352Z] ! auto-auth error: Scopes are required for this request.
[2018-06-05T12:15:17.352Z] > no credentials could be found or automatically retrieved
Error: Command requires authentication, please run firebase login
A minor clue is that the access token is empty (I have the same issue, I decoded the JWT)
Its implied from its form
xxxx.x.xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx-xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
The middle x is the data payload and is 1 character in size, so clearly is not very full.
firebase-tools uses google-auto-auth to get token so I think the problem might be there.
Whoops, the new version (3.18.6) still doesn't appear to pass authScopes to autoAuth(). If I add a log statement before this line: https://github.com/firebase/firebase-tools/blob/b2594467d8980c5a1e2b8c4aff3de9877a98b42b/lib/requireAuth.js#L21
I get authScopes: undefined.
If I add
authScopes = [
scopes.EMAIL,
scopes.OPENID,
scopes.CLOUD_PROJECTS_READONLY,
scopes.FIREBASE_PLATFORM,
];
before that line, then it proceeds to acquire an access token, but fails with PROJECT_NOT_FOUND
Also @tomlarkworthy, that OAuth token is not JWT, so it shouldn't contain the middle part. If you run it in https://developers.google.com/apis-explorer/#search/oauth2/oauth2/v2/oauth2.tokeninfo, it reports as a valid token with "scope": "https://www.googleapis.com/auth/cloudplatformprojects.readonly https://www.googleapis.com/auth/plus.me https://www.googleapis.com/auth/firebase https://www.googleapis.com/auth/userinfo.email",
Thanks! OK So when I get the project not found error. When I decode the token I have only a single scope "https://www.googleapis.com/auth/cloud-platform".
There is a difference between a "normal" token (i.e. one acquired through firebase login):
{
"issued_to": "563584335869-fgrhgmd47bqnekij5i8b5pr03ho849e6.apps.googleusercontent.com",
"audience": "563584335869-fgrhgmd47bqnekij5i8b5pr03ho849e6.apps.googleusercontent.com",
"user_id": "xxxyyy",
"scope": "https://www.googleapis.com/auth/userinfo.email https://www.googleapis.com/auth/cloudplatformprojects.readonly https://www.googleapis.com/auth/firebase https://www.googleapis.com/auth/plus.me",
"expires_in": 3484,
"email": "[email protected]",
"verified_email": true,
"access_type": "offline"
}
and one generated from a service account (SA):
{
"issued_to": "1160xxxx",
"audience": "1160xxxx",
"user_id": "1160xxxx",
"scope": "https://www.googleapis.com/auth/cloudplatformprojects.readonly https://www.googleapis.com/auth/plus.me https://www.googleapis.com/auth/firebase https://www.googleapis.com/auth/userinfo.email",
"expires_in": 3563,
"email": "[email protected]",
"verified_email": true,
"access_type": "offline"
}
So it appears that the token is not issued to the right audience and user_id, which should be the one from https://github.com/firebase/firebase-tools/blob/376678fef91f71de5859f14d8374b2d8d2731980/lib/api.js#L84
@tomlarkworthy still strange, my authScope is undefined unless I explicitly add the right scopes. Did you firebase logout before running this one?
OK that client ID is the oath2 client, which has very specific domains that it can work configured out of reach of us. And/or requires user interaction on localhost. So thats very hard to get authorization on in CI.
I am running mine on a function. I did not have the same error as you. I have project not found like the original poster.
If I construct my own token form the service account and pass it in with --token, I get:-
HTTP RESPONSE 401 vary=X-Origin, Origin,Accept-Encoding, www-authenticate=Bearer realm="https://accounts.google.com/", content-type=application/json; charset=UTF-8, date=Thu, 07 Jun 2018 00:16:43 GMT, expires=Thu, 07 Jun 2018 00:16:43 GMT, cache-control=private, max-age=0, x-content-type-options=nosniff, x-frame-options=SAMEORIGIN, x-xss-protection=1; mode=block, server=GSE, alt-svc=quic=":443"; ma=2592000; v="43,42,41,39,35", accept-ranges=none, connection=close
[2018-06-07T00:16:43.786Z] <<< HTTP RESPONSE BODY error=unauthorized_client, error_description=Unauthorized
[2018-06-07T00:16:43.791Z] > command requires scopes: ["email","openid","https://www.googleapis.com/auth/cloudplatformprojects.readonly","https://www.googleapis.com/auth/firebase"]
[2018-06-07T00:16:43.792Z] > authorizing via --token option
[2018-06-07T00:16:43.792Z] > refreshing access token with scopes: ["email","openid","https://www.googleapis.com/auth/cloudplatformprojects.readonly","https://www.googleapis.com/auth/firebase"]
[2018-06-07T00:16:43.793Z] >>> HTTP REQUEST POST https://www.googleapis.com/oauth2/v3/token
{ refresh_token: 'ya29.c.XXXXXXXXXXXX',
client_id: '563584335869-fgrhgmd47bqnekij5i8b5pr03ho849e6.apps.googleusercontent.com',
client_secret: 'j9iVZfS8kkCEFUPaAeJV0sAi',
grant_type: 'refresh_token',
scope: 'email openid https://www.googleapis.com/auth/cloudplatformprojects.readonly https://www.googleapis.com/auth/firebase' }
I think this oath client id is getting in the way ?
@tomlarkworthy not necessarily hard - I'm testing the configuration with clientId now.
Oh you can override these values:
https://github.com/firebase/firebase-tools/blob/376678fef91f71de5859f14d8374b2d8d2731980/lib/api.js
I tried creating a custom project with its own oauth client and override the firebase-tools client_id and secret_id. Then I autheorized the oath web application, copied the token and used it to invoke firebase-tools. It goes a slightly different path and successfully refreshes the token but then fails to get the list of projects. I confirmed in the token decoder it had the cloudplatformprojects readonly scope so it should have been able to read them.
info: stderr: [2018-06-07T01:02:21.126Z] Env Overrides: FIREBASE_CLIENT_ID, FIREBASE_CLIENT_SECRET
[2018-06-07T01:02:21.126Z] ----------------------------------------------------------------------
info: stderr: [2018-06-07T01:02:21.138Z] > command requires scopes: ["email","openid","https://www.googleapis.com/auth/cloudplatformprojects.readonly","https://www.googleapis.com/auth/firebase","https://www.googleapis.com/auth/cloud-platform"]
info: stderr: [2018-06-07T01:02:21.138Z] > authorizing via --token option
[2018-06-07T01:02:21.140Z] > refreshing access token with scopes: ["email","openid","https://www.googleapis.com/auth/cloudplatformprojects.readonly","https://www.googleapis.com/auth/firebase","https://www.googleapis.com/auth/cloud-platform"]
[2018-06-07T01:02:21.140Z] >>> HTTP REQUEST POST https://www.googleapis.com/oauth2/v3/token
{ refresh_token: 'ya29.XXX',
client_id: '278696186940-fbqtl733l62g4qj8aekr4i66cpo0k5c1.apps.googleusercontent.com',
client_secret: 'XXXX',
grant_type: 'refresh_token',
scope: 'email openid https://www.googleapis.com/auth/cloudplatformprojects.readonly https://www.googleapis.com/auth/firebase https://www.googleapis.com/auth/cloud-platform' }
Wed Jun 06 2018 18:02:21 GMT-0700 (PDT)
info: stderr: [2018-06-07T01:02:21.318Z] <<< HTTP RESPONSE 200 x-google-netmon-label=/bns/ph/borg/ph/bns/apiserving/prod_hightraffic_api_frontend.server/998, x-google-gfe-backend-request-info=eid=HYQYW5jODYyytgbB3JfoAg, cache-control=no-cache, no-store, max-age=0, must-revalidate, pragma=no-cache, expires=Mon, 01 Jan 1990 00:00:00 GMT, date=Thu, 07 Jun 2018 01:02:21 GMT, vary=X-Origin, Origin,Accept-Encoding, x-google-session-info=GgIYBiAB, content-type=application/json; charset=UTF-8, x-content-type-options=nosniff, x-frame-options=SAMEORIGIN, x-xss-protection=1; mode=block, server=GSE, x-google-servertype=apiserving, x-google-gfe-request-trace=acsfoh11:443,phnm21-v6:9897,/bns/ph/borg/ph/bns/apiserving/prod_hightraffic_api_frontend.server/998,phnm21-v6:9897,acsfoh11:443, x-google-gslb-service=apiserving-hightraffic, x-google-backends=plbn61:9882,/bns/ph/borg/ph/bns/apiserving/prod_hightraffic_api_frontend.server/998,phnm21-v6:9897,/bns/ph/borg/ph/bns/traffic-prod/shared-layer2-gfe/495,acsfoh11:443, x-google-dos-service-trace=main:identity-o-auth-2-service-migration,main:shared-layer2-gfe, x-google-service=identity-o-auth-2-service-migration,restricted-shared-layer2-grpc-aggregate, x-google-gfe-response-code-details-trace=response_code_set_by_backend,response_code_set_by_backend, x-google-gfe-response-body-transformations=gunzipped, x-google-shellfish-status=CA0gBEBG, alt-svc=quic=":443"; ma=2592000; v="43,42,41,39,35", x-google-gfe-service-trace=identity-o-auth-2-service-migration,restricted-shared-layer2-grpc-aggregate, accept-ranges=none, connection=close
info: stderr: [2018-06-07T01:02:21.319Z] >>> HTTP REQUEST GET https://admin.firebase.com/v1/projects/docsite-go
Wed Jun 06 2018 18:02:21 GMT-0700 (PDT)
info: stderr: [2018-06-07T01:02:21.652Z] <<< HTTP RESPONSE 404 server=nginx, date=Thu, 07 Jun 2018 01:02:21 GMT, content-type=application/json; charset=utf-8, content-length=87, connection=close, x-content-type-options=nosniff
info: stderr: [2018-06-07T01:02:21.652Z] <<< HTTP RESPONSE BODY code=PROJECT_NOT_FOUND, message=The specified project was not found.
@tomlarkworthy overriding client_id and secret with custom values won't work, because Firebase currently uses a pre-defined client that's separate from any customer projects (at least that's my understanding).
In addition, the --token option only supports refresh token, which you don't get if you have a service account (again, as far as I understand).
We need to find a simple way to generate the SA access token with this client ID, if possible.
It may be possible to go an alternate route and call Firebase APIs with a client JWT instead of OAuth token, as described here: https://developers.google.com/identity/protocols/OAuth2ServiceAccount#jwt-auth
google/google-auth-library-nodejs, which is used internally by stephenplusplus/google-auto-auth, provides a more convenient/secure method to do this.
I do not think we can make progress.
https://github.com/firebase/firebase-tools/issues/647#issuecomment-361926336 seems to have reported success previously, though not sure if that's confirmed. It does appear that the Firebase API in question (https://admin.firebase.com/v1/projects) is private, and only accepts tokens generated for that client ID.
Perhaps this should be filed as a feature request - having an ability to use a service account for deployment would enable using a single credential (and de-coupled from any user) to deploy both Firebase and GCP resources.
The --token option in the CLI is meant to be passed a refresh token, not an access token. It's the one that gets generated from firebase login:ci.
I haven't tested service account authorization extensively, but I suspect that there may be a broad-permission-requiring IAM check happening in the admin.firebase.com backend. We can investigate further, but I would not necessarily expect super-fast resolution here.
The --token option in the CLI is meant to be passed a refresh token
Yep, understood as mentioned above.
It would be amazing to use a SA key to deploy from CI environments. Refresh token is tied to a particular user, and it's not clear how to use it to authenticate gcloud commands to administer other GCP services. Currently, we have to supply both types of credentials (admin user's refresh token for Firebase CLI, and a SA key for gcloud).
I am able to FIREBASE_TOKEN='<token_here>' firebase deploy --only firestore,storage (I haven't tried other targets, it's possible they work) using a token generated for a service account.
The actual token was generated for a service account by vault's GCP secrets engine with the "https://www.googleapis.com/auth/cloud-platform" scope.
I confirm that it is impossibile to use a SA key + GOOGLE_APPLICATION_CREDENTIALS, with the latest firebase cli, any commands exit with:
root@frontend:/usr/src/app$ firebase list
Error: HTTP Error: 404, The specified project was not found.
Having trouble? Try firebase list --help
@cpick that's interesting, do you know how vault generate oauth tokens for service account ?
@paolomainardi firebase list won't work with an SA key because it depends on a legacy project listing implementation. However, just about everything else ought to (though you may need to enable a few APIs first). I'd recommend trying another command and see.
We are working on getting full support for GOOGLE_APPLICATION_CREDENTIALS without jumping through a bunch of hoops because we think it unlocks some great use cases.
@paolomainardi I think the vault implementation is here (that's just a guess after a quick search through its code).
I also think that's the same thing gcloud alpha iam service-accounts sign-jwt does (again, a somewhat educated guess).
Thanks a lot @cpick, i'll keep you posted.
I took a brief look at this and as a test tried to force through a service account credentials and an access_token into requireAuth.js
in an attempt to atleast see something work.
It seems the cli always attempts to contact https://admin.firebase.com/v1/projects/ no matter what (you can what i mean w/ the --debug flag. If i read into the previous comment in this issue, it maybe the 'legacy' api endpoint that doesnt' work with svc accounts.
I did test some other endpoints w/ simple GET calls and they seem to be ok:
for ref
- Hardcoded modification i made to
requireAuth.jsjust for testing that'll return a svc_accounts access token w/ wide scopes
function getServiceAccountClient() {
const credFile = '/path/to/cert.json';
const keys = require(credFile);
let client = new JWT(
keys.client_email,
null,
keys.private_key,
["email","openid","https://www.googleapis.com/auth/cloud-platform", "https://www.googleapis.com/auth/cloudplatformprojects.readonly","https://www.googleapis.com/auth/firebase"],
);
return client;
};
function _autoAuth(options, authScopes) {
return new Promise(function(resolve, reject) {
var client = getServiceAccountClient();
client.getAccessToken().then(res => {
console.log(res);
api.setAccessToken(res.token);
resolve();
}).catch(function (error) {
console.error('Unable to recall targetClient access_token ' + error);
});
/*
logger.debug("> attempting to authenticate via app default credentials");
......
- Generic Client
const {JWT} = require('google-auth-library');
function getServiceAccountClient() {
const credFile = '/path/to/cert.json';
const keys = require(credFile);
let client = new JWT(
keys.client_email,
null,
keys.private_key,
["email","openid","https://www.googleapis.com/auth/cloud-platform", "https://www.googleapis.com/auth/cloudplatformprojects.readonly","https://www.googleapis.com/auth/firebase"],
);
return client;
};
var client = getServiceAccountClient();
let project_id = 'your_project';
let url = 'https://admin.firebase.com/v1/projects/' + project_id
//let url = "https://firestore.googleapis.com/v1beta1/projects/" + project_id + "/databases/(default)/indexes"
//let url = "https://firebaserules.googleapis.com/v1/projects/" + project_id + "/rulesets"
client.requestAsync({url}).then(resp => {
console.log(resp.data);
}).catch(function (error) {
console.error('Unable to list buckets: ' + error);
});
I'm able to deploy finally using a service account to firestore, storage and hosting after making an edit to requireAuth.js as showin in this gist
The following is basically a hack and incomplete because it doesn't work with functions deployment. The full solution mentioned by mbleigh above for 'first class support` is worth waiting for.
Anyway, i verified it as follows:
Start with a firebase account thats also in context w/ gcloud
- Get a service account private key
$ gcloud iam service-accounts list
NAME EMAIL
App Engine default service account [email protected]
firebase-adminsdk firebase-adminsdk-h2v8k@firebase-auth-sal.iam.gserviceaccount.com
gcloud iam service-accounts keys create `pwd`/svc.json --iam-account=firebase-adminsdk-h2v8k@firebase-auth-sal.iam.gserviceaccount.com
Add the service account as
OWNERon that project- add firebase-adminsdk-h2v8k@firebase-auth-sal.iam.gserviceaccount.com as Owner of the project
(i'm pretty sure a lower permission set is good enough but i dint' look into that
- add firebase-adminsdk-h2v8k@firebase-auth-sal.iam.gserviceaccount.com as Owner of the project
Goto the cloud console and enable some APIs:
https://console.developers.google.com/apis/api/cloudresourcemanager.googleapis.com/overview?project=<your_project>
https://console.developers.google.com/apis/api/firebasehosting.googleapis.com/overview?project=<your_project>
- Remove local credentials
For both gcloud and firebase
$ firebase logout
✔ Logged out from [email protected]
$ mv ~/.config/gcloud ~/.config/gcloud_backup
- Set
ADCenv-var and deploy
export GOOGLE_APPLICATION_CREDENTIALS=`pwd`/svc.json
$ firebase deploy -P firebase-auth-sal --only firestore,hosting,storage
{ token: 'ya29.c.EmJ8B....', res: null }
=== Deploying to 'firebase-auth-sal'...
i deploying storage, firestore, hosting
i storage: checking storage.rules for compilation errors...
✔ storage: rules file storage.rules compiled successfully
i firestore: checking firestore.rules for compilation errors...
i firestore: reading indexes from firestore.indexes.json...
✔ firestore: rules file firestore.rules compiled successfully
i storage: uploading rules storage.rules...
i firestore: uploading rules firestore.rules...
✔ firestore: deployed indexes in firestore.indexes.json successfully
i hosting[fir-auth-sal]: beginning deploy...
i hosting[fir-auth-sal]: found 1 files in public
✔ hosting[fir-auth-sal]: file upload complete
✔ storage: released rules storage.rules to firebase.storage/firebase-auth-sal.appspot.com
✔ firestore: released rules firestore.rules to cloud.firestore
i hosting[fir-auth-sal]: finalizing version...
✔ hosting[fir-auth-sal]: version finalized
i hosting[fir-auth-sal]: releasing new version...
✔ hosting[fir-auth-sal]: release complete
✔ Deploy complete!
Project Console: https://console.firebase.google.com/project/firebase-auth-sal/overview
Hosting URL: https://fir-auth-sal.firebaseapp.com
- Verify Deployment
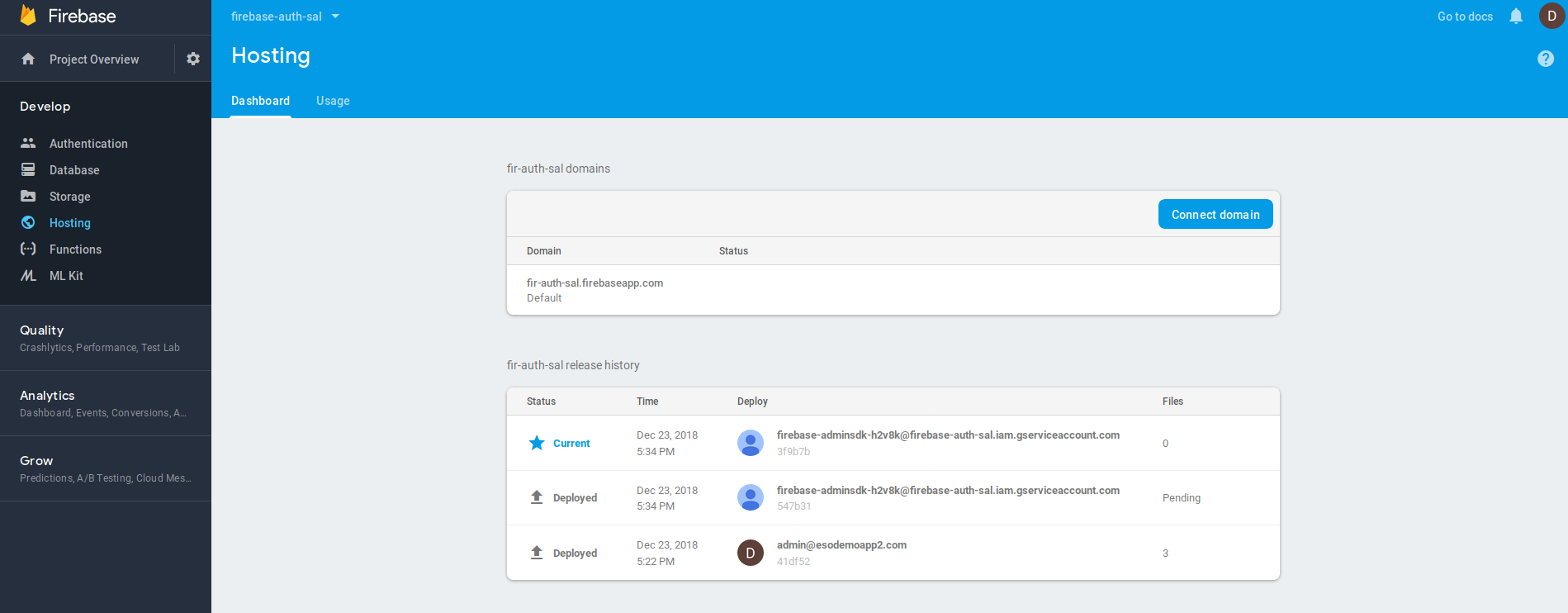
- Attempt
functionsdeployment
functions deployment types don't work even if i tried to override the enablement checks below (it halts on accessing some other mobilesdk.googleapis.com endpoint. It maybe the firebase functions deployments is tied to the client_id for firebase functions or somehow requires 3LO....but thats all conjecture
$ firebase deploy -P firebase-auth-sal --only functions --debug
[2018-12-24T01:36:44.034Z] >>> HTTP REQUEST GET https://servicemanagement.googleapis.com/v1/services/cloudfunctions.googleapis.com/projectSettings/firebase-auth-sal?view=CONSUMER_VIEW
[2018-12-24T01:36:44.034Z] >>> HTTP REQUEST GET https://servicemanagement.googleapis.com/v1/services/runtimeconfig.googleapis.com/projectSettings/firebase-auth-sal?view=CONSUMER_VIEW
[2018-12-24T01:36:44.486Z] <<< HTTP RESPONSE 404 vary=X-Origin, Referer, Origin,Accept-Encoding, content-type=application/json; charset=UTF-8, date=Mon, 24 Dec 2018 01:36:44 GMT, server=ESF, cache-control=private, x-xss-protection=1; mode=block, x-frame-options=SAMEORIGIN, x-content-type-options=nosniff, alt-svc=quic=":443"; ma=2592000; v="44,43,39,35", accept-ranges=none, connection=close
[2018-12-24T01:36:44.486Z] <<< HTTP RESPONSE BODY code=404, message=Method not found., status=NOT_FOUND
Error: HTTP Error: 404, Method not found.
[2018-12-24T01:36:44.495Z] Error Context: {
"body": {
"error": {
"code": 404,
"message": "Method not found.",
"status": "NOT_FOUND"
Internal bug reference: 122552119
Are there any updates on this issue @tinaliang ? I think that service account support for authentication should be high priority.
No update at this time...
My finding from last days is that I don't need specifically Firebase Cloud functions so I can use GCP Cloud functions https://cloud.google.com/functions/ which work as expected (deployment is done via gcloud CLI) However, this is not the real workaround ... but it might be helpful for someone :)
Duplicated by #1175
Are there any updates yet? I tried to deploy my Firebase app via Cloud Build. hosting etc. seems to work and deploy properly. functions wouldn't deploy correctly and I get the 404, as described above, with proper configuration within IAM. (The service account cloudbuild has rights to "Firebase Admin" and "API Keys Admin".) This ticket should have high priority 🔥
No updates yet, but we're hoping to take a look at it soon.
@mbleigh any update? confirming as of now firebase CLI cannot use a service account to deploy? we want it for CI tool. so GOOGLE_APPLICATION_CREDENTIALS support doesn't work?
As mentioned before, not all of the firebase CLI commands will work with GOOGLE_APPLICATION_CREDENTIALS, but a good number should. Setting it to the path of your service account credentials should be all you need to do (in fact, that's what the test-hosting.sh script does, among other things).
Using firebase login:ci you should be able to use a token in your CI system
Formalizing the usage and capabilities of GOOGLE_APPLICATION_CREDENTIALS is on our minds, but we cannot commit to a timeline on it. Thanks for your patience.
Could you clarify - would instance metadata ADC work in this case, or only GOOGLE_APPLICATION_CREDENTIALS?
Anyone on this thread: if you're feeling adventurous I'd love to have you try out the branch on #1463 and see if it lets you do the things you're looking to do with service account auth. I think we may have shored up the majority of issues, but I'd love to have some external testing of such.
@mbleigh firebase apps:list web will fail intermittently half of the time in Cloud Build. Running with debug doesn't give us any information on reason for failure. Any thoughts on what could be the case?
[2020-02-13T21:25:55.987Z] ----------------------------------------------------------------------
[2020-02-13T21:25:55.991Z] Command: /usr/local/bin/node /workspace/node_modules/.bin/firebase apps:list web -j --project=projectName --debug
[2020-02-13T21:25:55.991Z] CLI Version: 7.12.1
[2020-02-13T21:25:55.991Z] Platform: linux
[2020-02-13T21:25:55.991Z] Node Version: v10.18.0
[2020-02-13T21:25:55.992Z] Time: Thu Feb 13 2020 21:25:55 GMT+0000 (Coordinated Universal Time)
[2020-02-13T21:25:55.992Z] ----------------------------------------------------------------------
Also, @mbleigh firebase use projectName command will also intermittently fail because it fails to pull the right credentials from the metadata server:
[2020-02-13T21:49:41.050Z] ----------------------------------------------------------------------
[2020-02-13T21:49:41.055Z] Command: /usr/bin/node /directory/node_modules/.bin/firebase --debug use projectName
[2020-02-13T21:49:41.056Z] CLI Version: 7.12.1
[2020-02-13T21:49:41.056Z] Platform: linux
[2020-02-13T21:49:41.056Z] Node Version: v10.16.3
[2020-02-13T21:49:41.056Z] Time: Thu Feb 13 2020 21:49:41 GMT+0000 (Coordinated Universal Time)
[2020-02-13T21:49:41.056Z] ----------------------------------------------------------------------
[2020-02-13T21:49:41.057Z]
[2020-02-13T21:49:41.073Z] > command requires scopes: ["email","openid","https://www.googleapis.com/auth/cloudplatformprojects.readonly","https://www.googleapis.com/auth/firebase","https://www.googleapis.com/auth/cloud-platform"]
[2020-02-13T21:49:41.073Z] > attempting to authenticate via app default credentials
[2020-02-13T21:49:41.669Z] TypeError: Cannot create property 'refresh_token' on string 'Not Found
'
at /directory/node_modules/google-auto-auth/node_modules/google-auth-library/lib/auth/oauth2client.js:208:28
at /directory/node_modules/google-auto-auth/node_modules/google-auth-library/lib/auth/computeclient.js:85:7
at Request._callback (/directory/node_modules/google-auto-auth/node_modules/google-auth-library/lib/transporters.js:106:7)
at Request.self.callback (/directory/node_modules/request/request.js:185:22)
at Request.emit (events.js:198:13)
at Request.EventEmitter.emit (domain.js:448:20)
at Request.<anonymous> (/directory/node_modules/request/request.js:1161:10)
at Request.emit (events.js:198:13)
at Request.EventEmitter.emit (domain.js:448:20)
at IncomingMessage.<anonymous> (/directory/node_modules/request/request.js:1083:12)
at Object.onceWrapper (events.js:286:20)
at IncomingMessage.emit (events.js:203:15)
at IncomingMessage.EventEmitter.emit (domain.js:448:20)
at endReadableNT (_stream_readable.js:1145:12)
at process._tickCallback (internal/process/next_tick.js:63:19)
As of 10/02/20 I started seeing intermittent failures when using cloudbuild to deploy to firebase hosting when using a service account. It had been consistently fine for a while before that and now it seems it fails more often than not. I am starting to wonder if there is a new set of permissions I need to delegate to the service account so that it can do this successfully. It's become a bit of a problem as most of my deployments simply fail 😞
Below is a screenshot with an example of the builds and when they suddenly started failing:

The debug error is very similar to the comment above:
[2020-02-16T07:30:46.905Z] ----------------------------------------------------------------------
[2020-02-16T07:30:46.908Z] Command: /usr/local/bin/node /home/node/.npm-global/bin/firebase deploy --only hosting -P project-production --debug
[2020-02-16T07:30:46.908Z] CLI Version: 7.8.1
[2020-02-16T07:30:46.908Z] Platform: linux
[2020-02-16T07:30:46.909Z] Node Version: v12.13.1
[2020-02-16T07:30:46.909Z] Time: Sun Feb 16 2020 07:30:46 GMT+0000 (Coordinated Universal Time)
[2020-02-16T07:30:46.910Z] ----------------------------------------------------------------------
[2020-02-16T07:30:46.910Z]
[2020-02-16T07:30:46.920Z] > command requires scopes: ["email","openid","https://www.googleapis.com/auth/cloudplatformprojects.readonly","https://www.googleapis.com/auth/firebase","https://www.googleapis.com/auth/cloud-platform"]
[2020-02-16T07:30:46.920Z] > attempting to authenticate via app default credentials
[2020-02-16T07:30:47.023Z] TypeError: Cannot create property 'refresh_token' on string 'Not Found
'
at /home/node/.npm-global/lib/node_modules/firebase-tools/node_modules/google-auto-auth/node_modules/google-auth-library/lib/auth/oauth2client.js:208:28
at /home/node/.npm-global/lib/node_modules/firebase-tools/node_modules/google-auto-auth/node_modules/google-auth-library/lib/auth/computeclient.js:85:7
at Request._callback (/home/node/.npm-global/lib/node_modules/firebase-tools/node_modules/google-auto-auth/node_modules/google-auth-library/lib/transporters.js:106:7)
at Request.self.callback (/home/node/.npm-global/lib/node_modules/firebase-tools/node_modules/request/request.js:185:22)
at Request.emit (events.js:210:5)
at Request.EventEmitter.emit (domain.js:475:20)
at Request.<anonymous> (/home/node/.npm-global/lib/node_modules/firebase-tools/node_modules/request/request.js:1161:10)
at Request.emit (events.js:210:5)
at Request.EventEmitter.emit (domain.js:475:20)
at IncomingMessage.<anonymous> (/home/node/.npm-global/lib/node_modules/firebase-tools/node_modules/request/request.js:1083:12)
at Object.onceWrapper (events.js:299:28)
at IncomingMessage.emit (events.js:215:7)
at IncomingMessage.EventEmitter.emit (domain.js:475:20)
at endReadableNT (_stream_readable.js:1184:12)
at processTicksAndRejections (internal/process/task_queues.js:80:21)
Error: An unexpected error has occurred.
This seems to be related to https://github.com/firebase/firebase-tools/issues/1970 (namely, the deprecation of the old v1beta1 instance metadata endpoints, which are still used by the old gcloud Auth library used by Firebase CLI..)
Most helpful comment
@mbleigh any update? confirming as of now firebase CLI cannot use a service account to deploy? we want it for CI tool. so GOOGLE_APPLICATION_CREDENTIALS support doesn't work?